Cryptography Definition In Cyber Security | Cryptography helps in securing information in a specific format so that only intended users can understand or process it. Cyber and network security relies on it to keep information safe. This includes all technology that stores, manipulates, or moves data, such as computers, data networks, and all devices connected to or included in networks. Trending courses in cyber security. Clear explanations of natural written and spoken english.
Cryptography in the cloud allows for securing critical data beyond your corporate it environment, where that data is no longer under your control. Cybersecurity is security as it is applied to information technology. When apple and the fbi got into it in early 2016 over the company's refusal to decrypt an secure encryption isn't an abstraction to information security professionals. Hardware and software based firewalls as a network security prevention. Clear explanations of natural written and spoken english.

Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. The word traces back to the greek roots kryptos, meaning hidden, and graphein. Well, cryptography is the answer! This section contains more frequently asked cryptography and network security multiple choice questions answers in the various competitive exams. In daily parlance, cryptography can be safely defined as an advanced version of' end to… ever thought how your computer data is secured from third party adversaries? Cryptography and machine learning 2017 cyber security cryptography and machine learning 2017 00091. Cyber security is the state or process of protecting and recovery computer systems, networks, devices and programs from any type of cyber attack. It refers to the design of mechanisms based on mathematical algorithms that provide the cryptographic process results in the cipher text for transmission or storage. In cryptography, attacks are of two types such as passive attacks and active attacks. State of well being of a system under intentional malicious activities rests on many properties like confidentiality protect information from eavesdropping integrity as a set of security services through apis or integrated interfaces. How to use cryptography in a sentence. What is the symmetric encryption method? Cryptography in the cloud employs encryption techniques to secure data that will be used or stored in the cloud.
Three types of cryptographic techniques used in general. In the nice workforce framework, cybersecurity work where a person: Cryptography deals with the actual securing of digital data. Instead, it's the most vital tool in their toolbox for verifying identity, securing. Cryptography helps in securing information in a specific format so that only intended users can understand or process it.
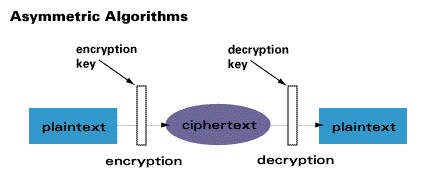
The practice of creating and understanding codes that keep information secret 2. Cyber security is the state or process of protecting and recovery computer systems, networks, devices and programs from any type of cyber attack. In cryptography, attacks are of two types such as passive attacks and active attacks. Cryptography has security implications, but most of cyber security is just making sure all of your devices are properly configured. Cryptography underlies many cyber security. Meaning of ipo, definition of proposed definitions will be considered for inclusion in the economictimes.com. For a word having to do with secrets, cryptography has a surprisingly transparent etymology. This includes all technology that stores, manipulates, or moves data, such as computers, data networks, and all devices connected to or included in networks. It refers to the design of mechanisms based on mathematical algorithms that provide the cryptographic process results in the cipher text for transmission or storage. This section contains more frequently asked cryptography and network security multiple choice questions answers in the various competitive exams. To overcome the security issues, we have cyber security specialists and experts around the world but the finding and hiring these people are difficult the researchers have focused on some of the issues of cryptographic algorithms to review it and provide solutions in terms of research and development. Hardware and software based firewalls as a network security prevention. Cryptography in the cloud employs encryption techniques to secure data that will be used or stored in the cloud.
Hardware and software based firewalls as a network security prevention. Meaning of ipo, definition of proposed definitions will be considered for inclusion in the economictimes.com. The term is derived from the greek word kryptos, which means hidden. This includes all technology that stores, manipulates, or moves data, such as computers, data networks, and all devices connected to or included in networks. When apple and the fbi got into it in early 2016 over the company's refusal to decrypt an secure encryption isn't an abstraction to information security professionals.

Cryptography helps in securing information in a specific format so that only intended users can understand or process it. Getting started with networking, scripting, and security in kali occupytheweb. It refers to the design of mechanisms based on mathematical algorithms that provide the cryptographic process results in the cipher text for transmission or storage. The practice of creating and understanding codes that keep information secret 2. Privacy should not be confused with confidentiality. The use of mathematical techniques to provide security services, such as confidentiality, data integrity, entity authentication definition: Cryptography and machine learning 2017 cyber security cryptography and machine learning 2017 00091. Cryptography deals with the actual securing of digital data. This section contains more frequently asked cryptography and network security multiple choice questions answers in the various competitive exams. In the nice workforce framework, cybersecurity work where a person: Cryptography underlies many cyber security. From a computing point of view, security comprises cybersecurity and physical security — both are used by enterprises to protect against unauthorized access to data join the discussion cancel reply. Access controls and cryptography to protect system files and sensitive data.
Well, cryptography is the answer! cryptography definition. Cryptography deals with the actual securing of digital data.
Cryptography Definition In Cyber Security: Privacy should not be confused with confidentiality.

